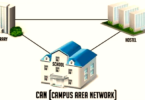
Computer networks link devices like computers, printers and routers via wired connections such as Ethernet or fiber optic cables or wireless signals like Bluetooth or Wi-Fi. This enables devices on the network to share resources efficiently.
Networking is an intricate combination of engineering, magic and skilled trade. It requires knowledge of its basics for anyone wishing to utilize modern services like Google search, instant messaging apps or social media.
Switches For Networking
Switches are devices used to connect devices on a network and are frequently found in small office or commercial environments. A network switch acts on the data link layer of the OSI model using MAC addresses to identify devices so it knows where to forward data packets. Error checking also takes place prior to data being sent out over its routed ports; unicast, multicast and broadcast communication modes can all be supported, and full duplex mode operates when used as part of this device’s functionality.

Network switches differ from hubs by being more intelligent in how they route network packets from receiver to sender – this helps minimize communication collisions while improving network performance and security.
Network switches operate at the data link layer of the OSI model and create separate collision domains for each port connected to them. When frames arrive at a switch, the device associated with that MAC address can be identified through reading it out of their header packet and consulting its internal MAC address table to see which port the target device belongs. It then transmits that packet.
Switches can filter incoming frames by inspecting their destination MAC addresses and only sending them out to ports associated with that MAC address, helping prevent unnecessary transmissions of information. Furthermore, if an unknown destination MAC address doesn’t match up in their internal MAC address table, flooding can be used to transmit the frame out across all ports except the one from which it came.
Network switches also offer features such as quality of service (QoS) and VLAN tagging that enable users to prioritize traffic and isolate groups of systems from each other, helping optimize bandwidth utilization and ensure performance in time-sensitive applications.
Routers
Routers serve to connect devices within and between networks. By analyzing a packet of data sent from one device to the next and identifying its optimal route, routers ensure your emails, web pages, and videos reach their destinations successfully.
They also enable wireless communication between networks, meaning your laptop or home computer can access work networks remotely through the Internet even when not located nearby – known as Virtual Private Network or VPN connectivity.
You need a router if you want to create a private network within your home or business that is isolated from the Internet and only accessible to devices connected directly to it, such as PCs and printers that share a room. Without one, connecting devices would require using switches or bridges – an expensive proposition indeed!
Routers operate at the 3rd Layer of OSI model and connect different networks together. A router uses its routing table to determine the best path for sending data to its destination and supports dynamic routing strategies through link-state and distance-vector protocols.
A router’s ability to filter packets and reduce collision domains makes it an invaluable asset in speeding up connections and decreasing collision domains. Furthermore, routers provide bridging functions, transferring data between two different networks, such as sending some incoming information to a WAN while routing others onto a LAN; this capability proves especially helpful in organizations needing to communicate with clients located across various geographies.
Wireless Access Points

Wireless Access Points (WAPs) are network devices that broadcast Wi-Fi signals, allowing devices to connect wirelessly to both the Internet and wired LAN networks. WAPs are widely used across both home and business networks; in particular, Wi-Fi wireless APs create networks that are easier for mobile users than their counterparts via wired infrastructure that require dedicated Ethernet cables for communication between switches and routers.
With the increasing use of portable devices like smartphones, tablets and laptops in both homes and businesses alike, wireless APs become increasingly useful in providing a stable connection. When trying to get Wi-Fi working properly across large areas such as office buildings or houses, many turn to them for help in making sure it functions seamlessly.
Multiple wireless APs can also be useful in homes and offices to ensure all areas have access to an internet connection, eliminating blackspots that prevent people from connecting properly – this can prevent irritating disconnections that keep some from getting online at all.
While there is a range of wireless APs to choose from, the one selected must meet the unique requirements of your network. MESH or MIMO technology could prove especially advantageous as these can increase signal strength while increasing data speeds to provide optimal performance for optimal network management.
Watch for features with guest access capabilities, which is particularly useful in offices. This enables visitors to the network without needing a password; some modern systems even include smart guest access controls that adhere to corporate security policies so you can decide what apps and services guests can access.
MAC Addressing
Every device that can connect to a network, from computers and printers to fax machines and printers, has an individual identifier known as a Media Access Control address (MAC for short). This address is assigned by your device’s Network Interface Controller (NIC), and used by switches as a means to direct data packets towards certain devices.
Every MAC address is globally unique and is burned into each NIC during device manufacturing. A MAC address consists of six outputs or octets, with three representing manufacturer identifiers and three being designated Organizationally Unique Identifier (OUI). Finally, three final octets identify which network adapter belongs to this device.
When a switch receives a frame on one of its ports, it compares the destination MAC address against its own list of stored addresses and forwards it if it matches; otherwise, it ignores it and does not forward it further.
MAC addresses also serve as a method to identify multicast addresses used by some network protocols like IPTV to deliver packets to all NICs that can handle them. A multicast MAC address has its own six-output format with individual addresses set as either bit 0 or 1 (to indicate group addresses or individuals), with group addresses having their bit set as either zero for individuals or one (ie group addresses). Since IP addresses operate at the network layer instead, and therefore multiple computers cannot use the same MAC address on one network simultaneously.
IP Addressing
IP addresses are unique identifiers that allow devices to connect to networks and include location data as well as two-way communication capabilities. Internet communications rely on IP addresses as a way of distinguishing among networks, routers and websites; without them, they would not exist!
Every network device has an IP address based on a numeric sequence. IP addresses can also be further subdivided using subnet masks – an additional level of sorting capabilities similar to zip codes – with each subnet mask signaling whether the remaining octets of an IP address belong to internal or public networks.
For two computers to communicate effectively with each other, they must share an IP address. A system known as Network Address Translation allows devices to travel between various network environments seamlessly.
Your computer automatically assigns itself an IP address when it connects with its ISP and the internet, but as you use your computer and access other networks (such as wireless hotspots in hotels or cafes), your temporary address changes accordingly.
When assigning IPv4 addresses via DHCP, they tend to try and keep their configuration as stable as possible – known in networking terms as being “sticky.” This helps with security as well as reduces the manual work required of network administrators when changes arise. As connected devices increase further still, sticky IP addresses become even more necessary due to IPv4 not being designed to handle such rapid expansion; luckily, IPv6 offers a more scalable and flexible design.