Welcome to the Ultimate Guide to Cyber security. In this digital period of time, it is important to prioritize your online security, so that you can protect yourself against a lot of attacks and threats. The main focus area, investment and for all sizes of businesses. Cyber security is important for both small and medium size businesses. Cyber security is involved in organizations computers, tablets and mobile phones.
What is Cyber Security:
Cyber security prevents IT networks, data, system and apps from threats and attacks. These types of threats and attacks mostly come from external attackers. Some of the types of attacks in cyber security include SQL injection, cross- site scripting attacks and session hijacking. It has a lot of tools and processes which help in the detection and blocking of threats. Cyber security department or team members run these tools and processes. This is important for hospitals, military cooperation, and organizations. Cyber security can reduce the risks and threats of attacks instead of defending against each type of attack.

Why is Cyber security Important?
Cyber security protects your business from cyber-threats. These threats consist of malware, phishing, code injections etc. Each type of attack has its own effects, which depends on the scope of the attack. Best security has the combination of hardware, best practices, data-backups and employee training. By using best- practices, knowing updates on threats and by taking cautious measures about our activities related to online presence. In this way we can reduce the risks of threats. In this way, we can keep such cyber-criminals away from us. So, be smart and keep yourself protected.
Types of Attacks in Network Security:
It is very important to use the security measures, which consists of preventing systems, firewalls, detection and VPN’s to prevent the network from the attacks.
Malware Threats:
Malware threat is such a type of thread which can damage your personal information and your devices. There are many types of Malwares such as viruses, Trojans, worms, adware spyware and many more.
Viruses can damage files on your devices, and worms can expand themselves across the networks. Trojans can give access to your data or device to the hackers. Spyware and adware can track your online activities without permission. For protecting yourself from threats, update your devices and security softwares. Do not download or open suspicious links or emails.
Phishing Attacks:
Phishing attacks are very common types of threats faced by individuals and organizations. These attacks include cyber criminals’ tricks of providing sensitive data or information, such as passwords, credit card numbers and personal identification numbers.
Phishing attacks are usually carried out through emails. For preventing yourself from these attacks, it is important to be vigilant whenever you receive unsolicited email. Using spam filters can minimize the risks of phishing attacks.
Denial-of- Services(DOS) Attacks:
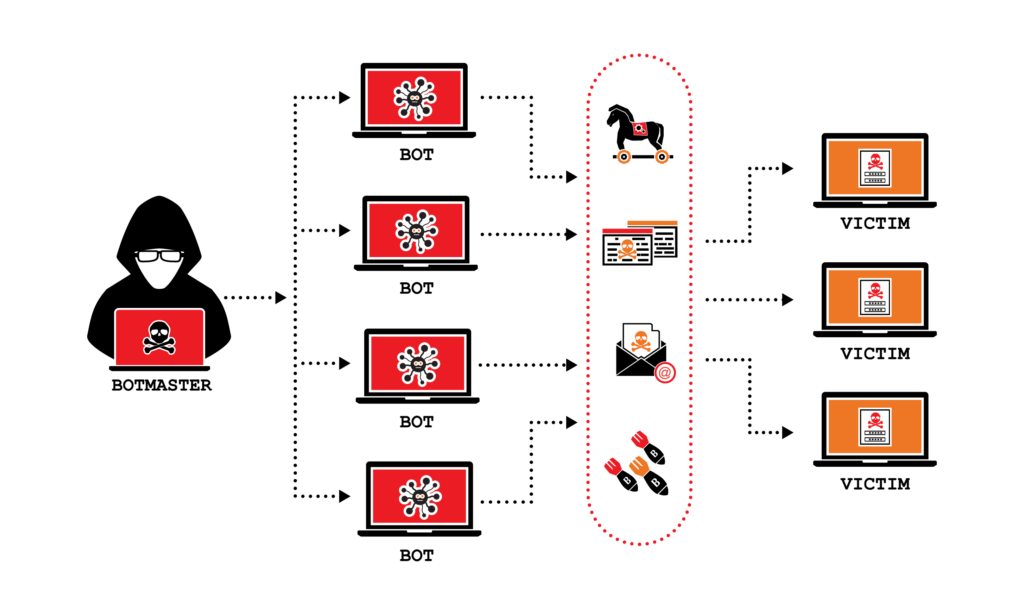
Denial-of- Services (DOS) attacks are such types of attacks that can overwhelm a system with excessive traffic, slow down or even shut-down the network. This type of attack results in the loss of services and trust of the customers. Cyber criminals use this type of attack to disturb the businesses normal operation and government organizations.
DOS attacks can also be used to disturb smoke screens for criminal activities. These attacks can overload routers, servers and other network resources. For reducing the impact of DOS attack, use the strategy of traffic filtering, load balancing solution and rate limiting.
Social Engineering Attacks:
Social Engineering attacks are the attacks which rely on psychological manipulation techniques. These attacks include phishing, pretexting and baiting.
To protect yourself from this type of attack, it is important to be aware of these tactics and must know how you can organize them. Always verify the legitimacy of any communication giving any kind of personal information. Be conscious of any unexpected offers especially from those whose requirement is to act quickly.
Insider Threats:
These types of threats can cause harmness to the company’s network by stealing their data by deleting their important files. This type of threat damages the company’s fame and reputation. To prevent yourself from insider threats; clear the security policies, conduct background checks and create strong security culture within the organization.
Jobs:
Within cyber security industry, there are many high-paying full -time jobs. For entry- level role, the employer salaries are between $70,000 and $90,000. Experienced security officers and directors can earn up to $150,000 annually. With so much demand for experienced and professionals of cyber security, you must have to choose this field.
Frequently Asked Questions:
QNo1: What is the most ideal way to teach myself cyber security?
Ans: With regards to finding out about cyber security, it means quite a bit to utilize a solid reliable source for cyber security preparation. Numerous offer courses in cyber security basics.
QNo2: Does cyber security need coding?
Ans: To emphasize, coding isn’t a necessity to start cyber security as a field. Assuming that you’re interested about where to start, you ought to begin with the internationally perceived CompTIA Security+ certificate.
QNo3: A non-IT individual learns cyber security?
Ans: The answer is No. Large numbers of the best security experts I know have non-specialized degrees like English, pre-Med, or even foundations in fields like technicians, visual creators, or housewives.
Conclusion:
Cyber security is very important to protect yourself against threats and attacks. By understanding various strategies and attack methods, you can protect your online presence. Your business’s success is relying on cyber security strategy. Regularly learn the latest security trends and best practices. It’s all up to you to play your role in keeping your online presence safe by being aware of various types of Cyber threats.